Unveiling Areas for Improvement in the Federal Reserve Banks' Information System Controls: A Comprehensive Guide

The Federal Reserve Banks (FRBs) play a pivotal role in the stability and integrity of the U.S. financial system. As custodians of sensitive financial data and critical infrastructure, maintaining robust information system controls is paramount to safeguarding the public's trust and preventing financial crimes.
4.6 out of 5
| Language | : | English |
| File size | : | 1172 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 19 pages |
| Lending | : | Enabled |
However, recent audit findings and regulatory examinations have identified areas where the FRBs' information system controls can be further enhanced. This comprehensive guide will delve into these areas, providing valuable insights and best practices for strengthening the resilience of the FRBs' financial operations.
Critical Areas for Improvement
1. Access Control and Authorization Management
Effective access control is crucial for preventing unauthorized access to sensitive data. The FRBs must strengthen their processes for granting, reviewing, and revoking user access privileges. This includes implementing multi-factor authentication, enforcing password complexity requirements, and establishing role-based access controls.

2. Data Security and Encryption
Protecting data at rest and in transit is essential to prevent data breaches and unauthorized disclosures. The FRBs should adopt encryption technologies such as AES-256 to safeguard sensitive financial data. Additionally, they must implement data loss prevention measures to prevent accidental or intentional data leakage.

3. System Monitoring and Logging
Continuous monitoring and logging of system activities provide invaluable insights for detecting and responding to security incidents. The FRBs should enhance their monitoring capabilities to identify suspicious activities, failed login attempts, and unauthorized system changes in real-time.

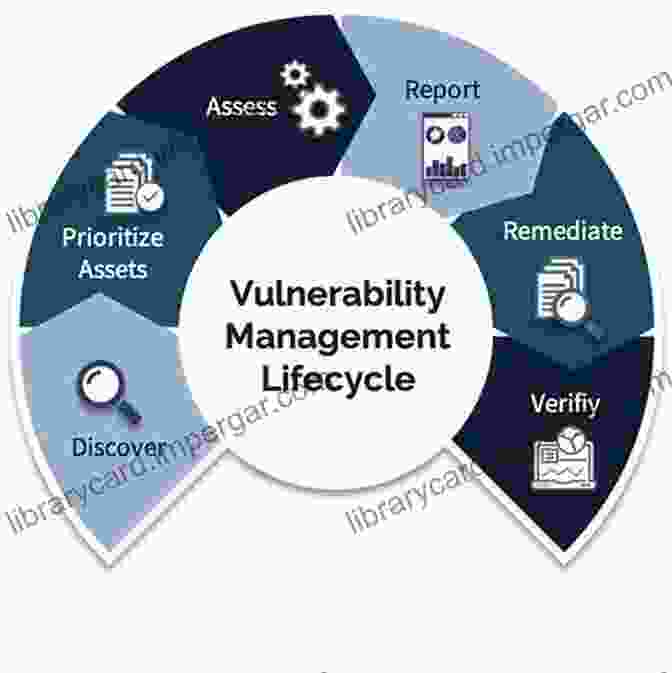
4. Vulnerability Management and Patching
Vulnerabilities in software and operating systems can provide entry points for cyberattacks. The FRBs must implement a comprehensive vulnerability management program that includes regular scanning for vulnerabilities, prioritizing fixes, and timely patching.
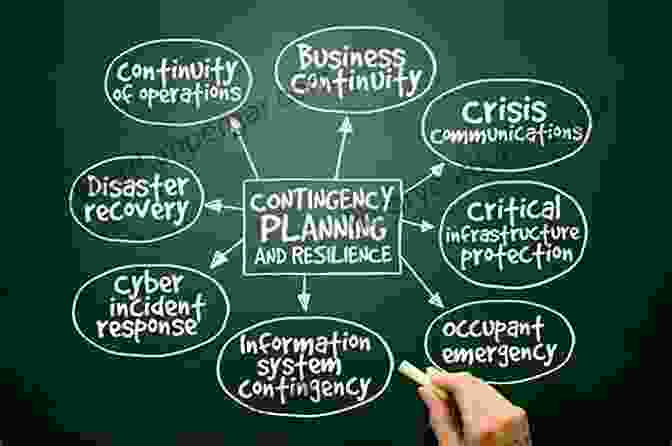
5. Disaster Recovery and Business Continuity Planning
Disasters and emergencies can disrupt operations and threaten data integrity. The FRBs must develop robust disaster recovery and business continuity plans that ensure the availability and accessibility of critical data and systems in the event of a disaster.
Best Practices and Recommendations
- Implement a risk-based approach: Prioritize control improvements based on the potential impact and likelihood of risks.
- Adopt industry best practices: Align controls with established standards such as the NIST Cybersecurity Framework, ISO 27001, and COBIT.
- Conduct regular internal audits: Regularly assess the effectiveness of information system controls and identify areas for improvement.
- Foster a culture of security awareness: Train employees on information security best practices and the importance of reporting suspicious activities.
- Collaborate with external experts: Consult with cybersecurity firms, auditors, and regulators to gain external perspectives and stay abreast of emerging threats.
Benefits of Enhanced Information System Controls
- Increased data protection: Reduces the risk of data breaches and unauthorized access.
- Improved regulatory compliance: Demonstrates adherence to regulatory requirements and industry standards.
- Enhanced operational resilience: Ensures the availability, integrity, and confidentiality of critical systems and data.
- Reduced financial losses: Prevents financial crimes and protects the FRBs from costly litigation and reputational damage.
- Increased public trust: Builds confidence in the FRBs' ability to safeguard financial stability and prevent financial crises.
Strengthening the Federal Reserve Banks' information system controls is not just a regulatory requirement but a strategic imperative for safeguarding the U.S. financial system. By addressing the critical areas for improvement identified in this guide, the FRBs can enhance their cybersecurity posture, protect customer data, and maintain the trust of the public. Embracing best practices and fostering a culture of security awareness will enable the FRBs to withstand evolving cyber threats and ensure the resilience of the financial infrastructure.
This comprehensive guide provides a roadmap for improving the FRBs' information system controls and achieving a robust and secure financial operating environment.
4.6 out of 5
| Language | : | English |
| File size | : | 1172 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 19 pages |
| Lending | : | Enabled |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Oscar E Gilbert
Oscar E Gilbert Amber Ault
Amber Ault Ellynanne Geisel
Ellynanne Geisel Richard Rinehart
Richard Rinehart Alexey Vasilyevich Trekhlebov
Alexey Vasilyevich Trekhlebov Jeffrey Glover
Jeffrey Glover Gordana Fontana Giusti
Gordana Fontana Giusti Alice Morse Earle
Alice Morse Earle Ali Mirsepassi
Ali Mirsepassi Arthur L Stinchcombe
Arthur L Stinchcombe Alyosha Goldstein
Alyosha Goldstein Aleksandar Stevanovic
Aleksandar Stevanovic Saransh Desai Chowdhry
Saransh Desai Chowdhry Michael Huemer
Michael Huemer Andrew James Hamilton
Andrew James Hamilton Mary Ingham
Mary Ingham Alexander Welsh
Alexander Welsh Benjamin Schoendorff
Benjamin Schoendorff Alessio Rozzi
Alessio Rozzi Bassam Loucas
Bassam Loucas
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Efrain Powell23 Life-Changing Stories: Break Free from the Grip of Dieting, Weight, and...
Efrain Powell23 Life-Changing Stories: Break Free from the Grip of Dieting, Weight, and...
 Dustin RichardsonUnveiling the Truth: Exposing the Establishment Media's Hidden Deals and...
Dustin RichardsonUnveiling the Truth: Exposing the Establishment Media's Hidden Deals and... Bryce FosterFollow ·12.6k
Bryce FosterFollow ·12.6k Eric HayesFollow ·19.6k
Eric HayesFollow ·19.6k Joseph FosterFollow ·4.8k
Joseph FosterFollow ·4.8k Adrian WardFollow ·9.5k
Adrian WardFollow ·9.5k Diego BlairFollow ·18.8k
Diego BlairFollow ·18.8k Maurice ParkerFollow ·14.1k
Maurice ParkerFollow ·14.1k Logan CoxFollow ·19.3k
Logan CoxFollow ·19.3k Jerry HayesFollow ·7.8k
Jerry HayesFollow ·7.8k

 Ignacio Hayes
Ignacio HayesUnveiling the Secret Spitfires: Britain's Hidden Civilian...
: The Untold Story of Britain's...

 Scott Parker
Scott ParkerLiving With Schizophrenia: A Father and Son's Journey
Schizophrenia is a serious...

 Ted Simmons
Ted Simmons"From Sign Up to Pass Out": The Shocking and Immersive...
Step into the...

 John Keats
John KeatsThe Development of Biographies and Philosophical...
The Alluring...

 Dan Brown
Dan BrownCapture Your Dream Wedding with Digital Wedding...
Your wedding day is...
4.6 out of 5
| Language | : | English |
| File size | : | 1172 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 19 pages |
| Lending | : | Enabled |